.webp)
FedRAMP: A simple guide to a strict cloud security standard
FedRAMP: A simple guide to a strict cloud security standard
At IriusRisk, we strive to provide the latest technical threat libraries based on published security standards. We released a new content library in version 3.11.0 which helps security and engineering teams build for FedRAMP compliance.In this article:
- We will walk through the basics of FedRAMP, impact levels and security objectives, and a snapshot of these in action within IriusRisk.
- It will be of particular importance and interest to organisations that provide cloud-based technologies to the US federal government.
What is FedRAMP?
The Federal Risk and Authorization Management Program (FedRAMP) is a US federal government programme that promotes the adoption of secure cloud services and technologies across government agencies. It does this using a standardised approach to security assessment, authorisation, and continuous monitoring of cloud service providers.
FedRAMP standardises these security requirements through a legal framework that incorporates FISMA, an older act passed in 2002 that led to the creation of NIST. Both FedRAMP and FISMA are based on NIST SP 800-53 baselines and contain controls, parameters, and guidance that address the unique components of cloud computing.
IriusRisk's approach to FedRAMP
FedRAMP’s requirements are applicable beyond IT teams and extend to business and operations units. In response, IriusRisk has built its FedRAMP library – a set of development requirements that aid compliance with FedRAMP Technical Security Controls Baselines. Known for being an incredibly strict and stringent standard, we have designed this library to aid security and engineering teams at the forefront of building the technology behind modern, competitive cloud service offerings. The library contains:
- AC: Access Control.
- AU: Audit and Accountability.
- IA: Identification and Authentication.
- SC: System and Communications Protection.
Explaining FedRAMP impact levels and associated risk
FedRAMP outlines three impact levels for cloud service offerings (CSOs) across three distinct security objectives.
Security objectives:
- Confidentiality: Protections for privacy and proprietary information.
- Integrity: Protections against modification or destruction of information.
- Availability: Timely and reliable access to data.
Impact levels:
- High (based on 421 controls): “High Impact data is usually in Law Enforcement and Emergency Services systems, Financial systems, Health systems, and any other system where loss of confidentiality, integrity, or availability could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.
- Moderate (based on 325 controls): “Where the loss of confidentiality, integrity, and availability would result in serious adverse effects on an agency’s operations, assets, or individuals. Serious adverse effects could include significant operational damage to agency assets, financial loss, or individual harm that is not loss of life or physical.” Nearly 80 percent of approved FedRAMP applications are considered moderate impact systems.
- Low (based on 125 controls): “where the loss of confidentiality, integrity, and availability would result in limited adverse effects on an agency’s operations, assets, or individuals.” FedRAMP contains two baselines for systems with low impact data (LI-SaaS Baseline and Low Baseline).
FedRAMP baseline security standards within IriusRisk
We have created and mapped three separate IriusRisk standards that consider FedRAMP impact levels: the Low, Moderate, and High Baselines – as seen below within the platform.

Below, a diagram for an AWS architecture that utilises the new IriusRisk FedRAMP component. This component was introduced in the v3.11.0 release and enables you to import the risk patterns related to FEDRamp.
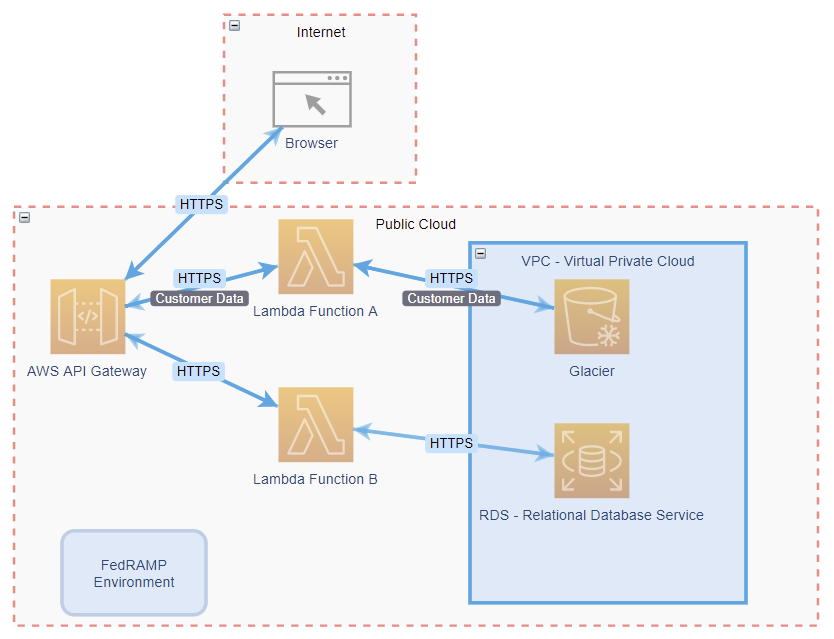
As with all IriusRisk standards, the countermeasures that are applicable to our AWS architecture threat model, and classified within FedRAMP standards, are automatically identified and generated.

The “compliance view” in IriusRisk can be used to see how the identified countermeasures map to the requirements of a standard.
- The “Non-Compliant” category lists the countermeasures that are required by the standard but have not been marked as requirements in the threat model.
- The “Required” countermeasures are those marked as requirements in the threat model and are also required by the standard. This essentially means that the team plans to implement them, but hasn’t done so yet.
- The “Implemented” category means that the team has indicated that the countermeasure has been implemented (usually achieved through the automatic two-way Jira sync).
- The “Verified” category means that the countermeasures have been tested and are verified to have been implemented.
The TL;DR
We’re happy to announce the release of our FedRAMP security standards library in v3.11 of IriusRisk.
FedRAMP Technical Security Controls are now part of our threat modeling tool – an accessible platform that supports security and compliance teams whilst ensuring that all technical FedRAMP requirements can be identified easily at design time and implemented accordingly.




