Contents
Risk types and their explanations
Weaknesses with no Countermeasures
While in your threat view, and after expanding some of the components, you will see three ellipses next to the threat name which will show you more options. Including, ‘Threat Details’.

If you select the Threat Details option, a Context Window will come up on the right hand side with further context about that threat. You can expand this window to the full screen if you wish. You can click from the threat into the corresponding countemreasure for easier navigation, and view them side by side.
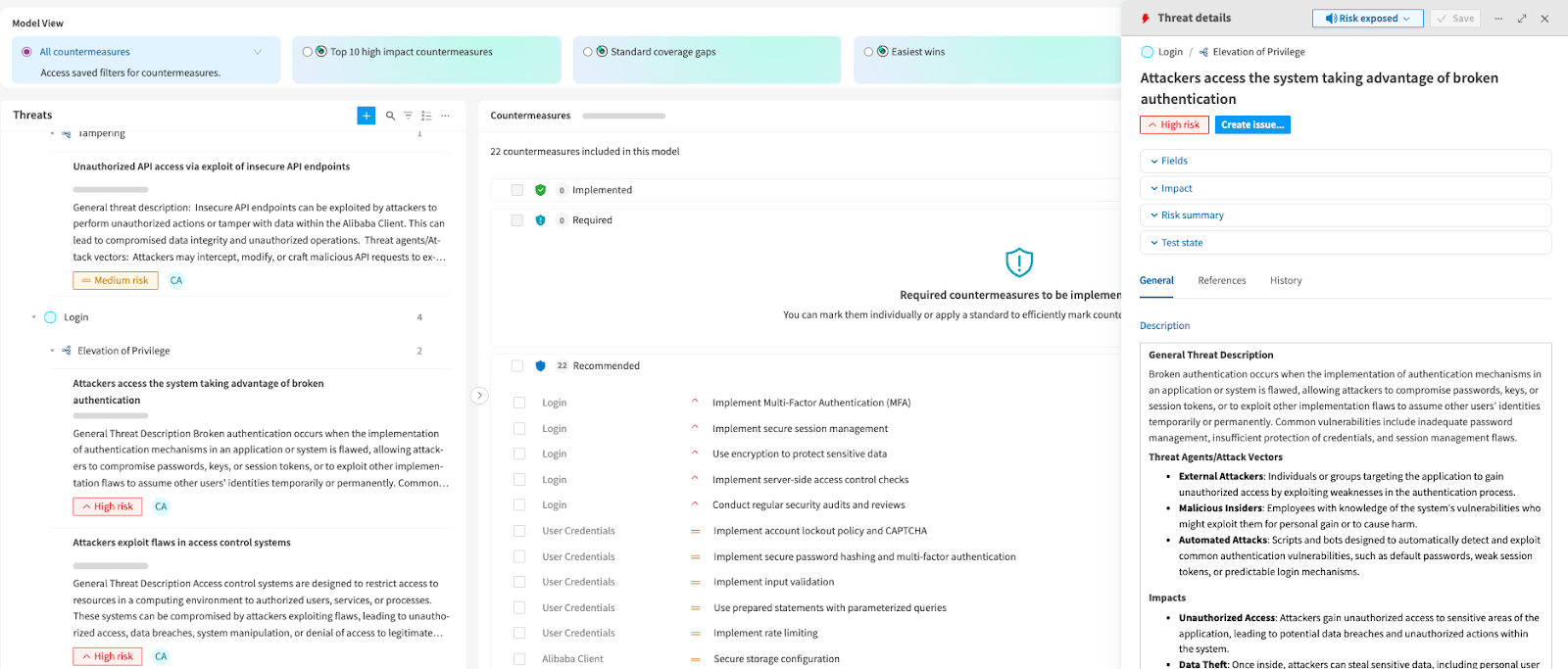
If you select the 'Threat Details' option, a box will come up with further context about that threat.

On the left you see the description of the threat and the level of threat - in this case, High Risk.
If you scroll down it also shows you countermeasures appropriate to any Common Weakness Remuneration (CWEs). You can add/ see Comments and history, as well as the link to more context of the CWE reference via an external URL. Comments are now consistently displayed from newest to oldest in both threat and countermeasure details. This is helpful for users especially where there have been a high number of comments, and it is required to have the most recent remarks seen first in order to be informed or see context straight away.
On the right hand side you have other expandable options, which are:
In this area, you can see the Project Owner, the reference ID which applies to the threat reference within this precise threat model. The source of the threat (the Rules Engine), any Issue ID’s - Issue Tracker Integration gets covered later on - as well as two useful mapping fields for MITRE and STRIDE-LM references.
In this example it has 8 Mitre references which can be seen if you hover over the field where it says +8… For STRIDE in this example the threat only relates to one STRIDE element, which is Tampering.

Scrolling down to Impact and expanding this area you will see it is based upon Confidentiality, Integrity and Availability (CIA), as well as Ease of Exploitation. This is to provide further context for decision making, when you choose which threats should be mitigated. As we know, not all risks can be removed due to budget and resources. So choosing the highest risk is where most people start. You can manually change these yourself and select a different option from each drop down - if you know enough about your threat model to be able to do this.

What is CIA? Confidentiality refers to the principle that only those who should have access to information can access it. Integrity refers to the principle that data is what we expect it to be, and Availability refers to the principle that data is reliably available.
Here you can view the Inherent, Current, and Projected Risk for the threat.

Inherent risk: This represents the risk natural to affected assets and its exposure. Inherent risk represents the complete risk with zero mitigations being applied to this given scenario.
Formula 1 - Inherent Risk = impact x likelihood
Current risk: This is the current risk value which is equal to inherent risk minus currently implemented mitigations or countermeasures.
Formula 2 - Current Risk = Inherent Risk - implemented mitigation
Projected risk: This is our goal risk, the one we will have once we have already implemented all required countermeasures. It's calculated by subtracting from the inherent risk the risk reduction produced for all implemented and required countermeasures.
Formula 3 - Projected Risk = Current risk - planned mitigations (countermeasures in a required status)
Test State: Threat Details

Here you see Countermeasures and Weaknesses, and whether they have been tested, and/ or passed, partially passed, failed and so on. To actually change the status, this is done so in the Countermeasures view, rather than the threat view.
Finally, if you do make any edits, don’t forget to press Save in the top right of the Threat Details Menu. You can also mark this threat as accepted or not applicable at the top of the menu where it says Risk Exposed.

Weaknesses with no countermeasures are now displayed in the Threat Detail modal. Prior to this update, users who manually added a weakness couldn’t view or delete it from the Threat Detail modal. This change is to remove frustration and make it clearer within this modal where there may be countermeasures to be added or included against a weakness.

Now it is time to move onto Countermeasures, and what we can do to mitigate the identified threats. Let’s move on to Question 3: What are we going to do about it?